- Introduction.
- Cyber Security for Remote Workers
- Best Practices for Remote Work Security
- Develop a remote security policy
- Manage passwords
- Use VPN
- Update software and devices
- Do not work on public networks
- Use reliable and secure services
- Conducting Videoconferences Safely
- Do not click on suspicious emails or texts
- Work on your work device
- Protecting Devices
- Use multi-factor authentication
- Encrypt your email
- Know how to contact Remote IT Security
- Keep your router up-to-date
- Is it possible to have 100% security while working remotely?
- How about security in the office?
- Transcribing audio into articles using interview AI
- summary
Introduction.
Security in remote work is an important issue for many remote workers.
This article presents 14 best practices to consider for enhancing remote work security.
Cyber Security for Remote Workers
As remote work expands, cybersecurity risks increase tenfold for employers. It is difficult to know what measures remote workers are taking, and security controls are often outlawed.
On the other hand, remote workers are frequent targets of cyber attacks. Personal security is often not as robust as an employer’s, and laptop, smartphone, and Wi-Fi passwords need to be considered. There is a lot to consider, and if remote work security is not taken seriously, everyone is at risk.
Common security weaknesses associated with remote work include
- Weak or duplicate passwords
- Unprotected devices
- Lack of backup system
- phishing
- Use of public Wi-Fi
- malware attack
Strengthening these weaknesses in both the company and the remote worker will help keep the team at peak productivity.
Best Practices for Remote Work Security
Remote work security may seem daunting given the statistic that “by 2023, data breaches had increased by 72% since 2021, when they hit an all-time high.” However, while no network is completely secure, a few best practices can significantly reduce the risk of harm to employers and remote workers.
Develop a remote security policy
It is important for employers to have a remote security policy in place and to ensure that all remote workers understand its contents. The policy should include, but not be limited to, the following
- Access and Network Authority: Clearly define who has access to what and when.
- Overview of security measures: Explains the use of VPNs, installation of firewalls, and the need for encryption.
- Policies and Procedures: Define password policies, software update requirements, and procedures for reporting lost or stolen software.
- Device Usage Guidelines: Establish guidelines for the use and security protection of work and personal devices and identify which devices are to be monitored.
- Policy Violation Policy Measures: Establish penalties for policy violations in remote environments.
Remote workers are expected to understand and practice the company’s remote data security policies and procedures.
Manage passwords
Everyone knows the importance of passwords, but they are especially important when working remotely. After all, you are not the only one handling the information.
Always include upper and lower case letters, numbers, and symbols (where allowed) in your passwords, and never use the same password for different logins. Ideally, use a reliable password generator such as NordPass or Strong Password Generator to create strong passwords.
Password managers such as NordPass and 1Password are convenient tools for creating, protecting, and sharing unique passwords, and are an easy security measure to enforce password protection.
Use VPN
A VPN (Virtual Private Network) provides a secure connection to another network; a VPN functions similarly to a firewall, ensuring that only authorized personnel can access the network.
A VPN provides the same level of cybersecurity at home as your office network, making remote workers more secure. You can download a VPN app for a few dollars a month, but be sure to check your company’s guidelines before downloading.
Update software and devices
Frequent software updates may be tiring, but there is a reason for the updates. Regular updates not only improve devices, they also fix security vulnerabilities. If you are unsure of the need, consult your company’s IT department.
Do not work on public networks
Insecure public networks are a prime target for hackers because they are full of easily accessible email accounts and passwords. If you just want to work at the local coffee shop, bring a secure hotspot.
More tips for working in public places
- Use a VPN for maximum security
- Ensure that the screen is not visible to others.
- Never click on “Show Password” when working in public.
Use reliable and secure services
We all use online and cloud-based services that make our jobs easier – services such as Adobe products, Google Docs, Microsoft 365, and many other collaboration tools are essential for many remote jobs, so be sure to know which services Be sure to know which services prioritize security.
Conducting Videoconferences Safely
With the rise of remote work, security breaches of remote meetings are on the rise. To enhance the security of your online meetings and mitigate cybersecurity risks, keep the following in mind
- Use a paid account that offers better security
- Lock after the meeting starts
- Create a unique ID and password for each meeting
- Utilize the waiting room feature, if provided by the service.
- Prohibit screen sharing by anyone other than the organizer or co-hosts
Do not click on suspicious emails or texts
Needless to say, do not open strange or suspicious emails. However, phishing scams are becoming increasingly sophisticated and difficult to spot, often perfectly mimicking trusted brands, services, and personal contact information.
The best defense against phishing scams is awareness. Therefore, a thorough company security team should send out notifications when a prominent scam is circulating. If in doubt, do not click.
Work on your work device
The company should have a policy regarding approved work devices, but it is a good idea to follow the rule of keeping work and personal devices separate.
In other words, if you are working on a work device, do not surf the web or shop online for personal reasons. Adding your credit card information, for whatever reason, increases your chances of being attacked. If you are attacked, you never know what else you may find. The less personal information you have stored on your device, the safer all of your information will be.
Protecting Devices
Do not leave your cell phone, tablet, or laptop unattended, even for a few seconds. It is much easier to steal a device than to hack it, so do not leave it where it is in danger of being stolen. This includes leaving them at the airport or on a table while working in a coffee shop. Not only will you lose your device, but all information stored on it will be exposed.
Use multi-factor authentication
While it is certainly a hassle to have to enter a code sent to your phone every time you log in to your work email, multi-factor authentication is an effective way to prevent hackers from gaining access to your account. If the service you are logging into for work tasks offers multi-factor authentication, we strongly recommend that you use it.
Encrypt your email
Email encryption prevents anyone other than the intended recipient from reading or viewing the contents of the email.
If an e-mail is hacked or accidentally sent to another person, encryption protects the e-mail because only the person with the decryption key can view the contents. Most e-mail services offer e-mail encryption options free of charge.
Know how to contact Remote IT Security
Remote workers should have their company’s security or IT department on speed dial, or at least know how to contact them quickly if they suspect they have been hacked or if they accidentally click on a suspicious link. The sooner you discover if there is a problem, the sooner you can begin to resolve it.
Keep your router up-to-date
Having discussed keeping devices up-to-date with the latest software and patches, it should be emphasized that these updates should not be limited to phones, tablets, and laptops.
Routers are as important to cybersecurity as, if not more so, than any other device. Keeping your router’s firmware up-to-date can help prevent security breaches that could affect all devices on your home or office network.
Most modern devices will notify you when updates are available, but your router may require proactive TLC.
To find out if an update is available, you will need to look up the model number of your router. Typically, the model number is printed on the back or bottom of the router. Then go online and search for “router firmware update” using the model number. You should then be able to easily find step-by-step instructions from the manufacturer. Bookmark the page and check it regularly.
Is it possible to have 100% security while working remotely?
No, it is impossible to be 100% secure while working remotely, but by following these cybersecurity tips for employees and employers, you can be as safe as possible.
From the security of movie and television sets to thecybersecurity of law firms, every workplace has security best practices, and remote work is no exception. Being a secure remote worker or securing a remote workforce should never be taken lightly.
How about security in the office?
In-office IT security and remote IT security are similar in that information is constantly moving wirelessly and needs to be protected. The general flow of that security is the same whether you work onsite or remotely. Protect passwords, work only on work devices, keep all devices up to date, and use only trusted and secure external services.
The difference between in-office security and remote work security is that it is theoretically easier to secure an office because you have more fine-grained control over employee behavior.
For example, you can prohibit the use of personal devices on company property. It is also easier to secure offices, as it tends to be easier for hackers and phishers to attack remote workers than it is for them to compromise the security of large corporate offices.
For office workers and remote workers who need to travel to the field from time to time, there are several other ways to ensure their own and others’ safety.
- Do not share your ID badge for any reason
- Do not share USB drives. Also, never plug in a USB drive that does not belong to you.
- When dealing with sensitive information, be careful that strangers do not look at the screen!
- Protect your belongings! You never know when thieves may be patrolling your office!
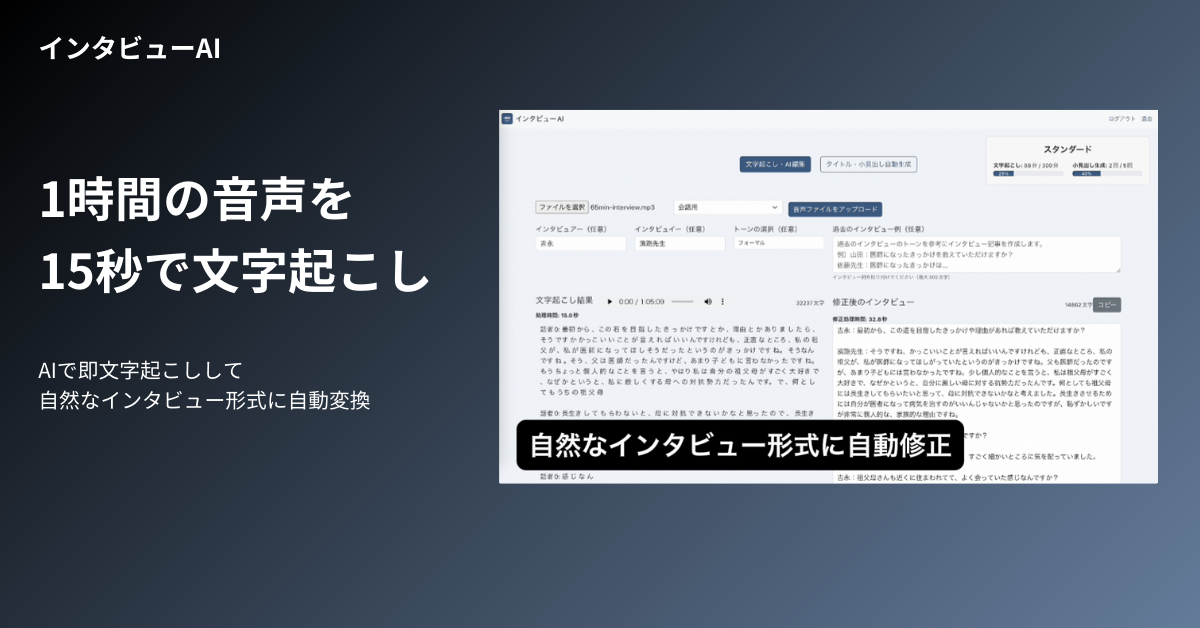
Transcribing audio into articles using interview AI
Once the interview questions have been developed using the above methods and the actual interviews have been conducted, it will be necessary to turn them into articles.
Interview AI transcribes an hour of audio in just 15 seconds and automatically converts it into a natural interview format. It also automatically creates summaries, titles, and subheadings, so you can complete your interview transcription with this tool.
summary
The importance of digital security in remote work is a constant concern. As long as the Internet exists, remote work will never be 100% secure. However, by following some personal best practices and adhering to your company’s remote work security policy, you can be as safe as possible.